StackGen Catalog
The StackGen Catalog is designed to provide you, as a DevOps team, with a powerful tool to curate and enforce the use of specific Terraform modules within your organization. By integrating trusted modules from various sources, including custom Git repositories, Terraform registries, and StackGen-generated modules, you can establish policies that ensure developers use only approved infrastructure configurations, thereby streamlining workflows and enhancing security.
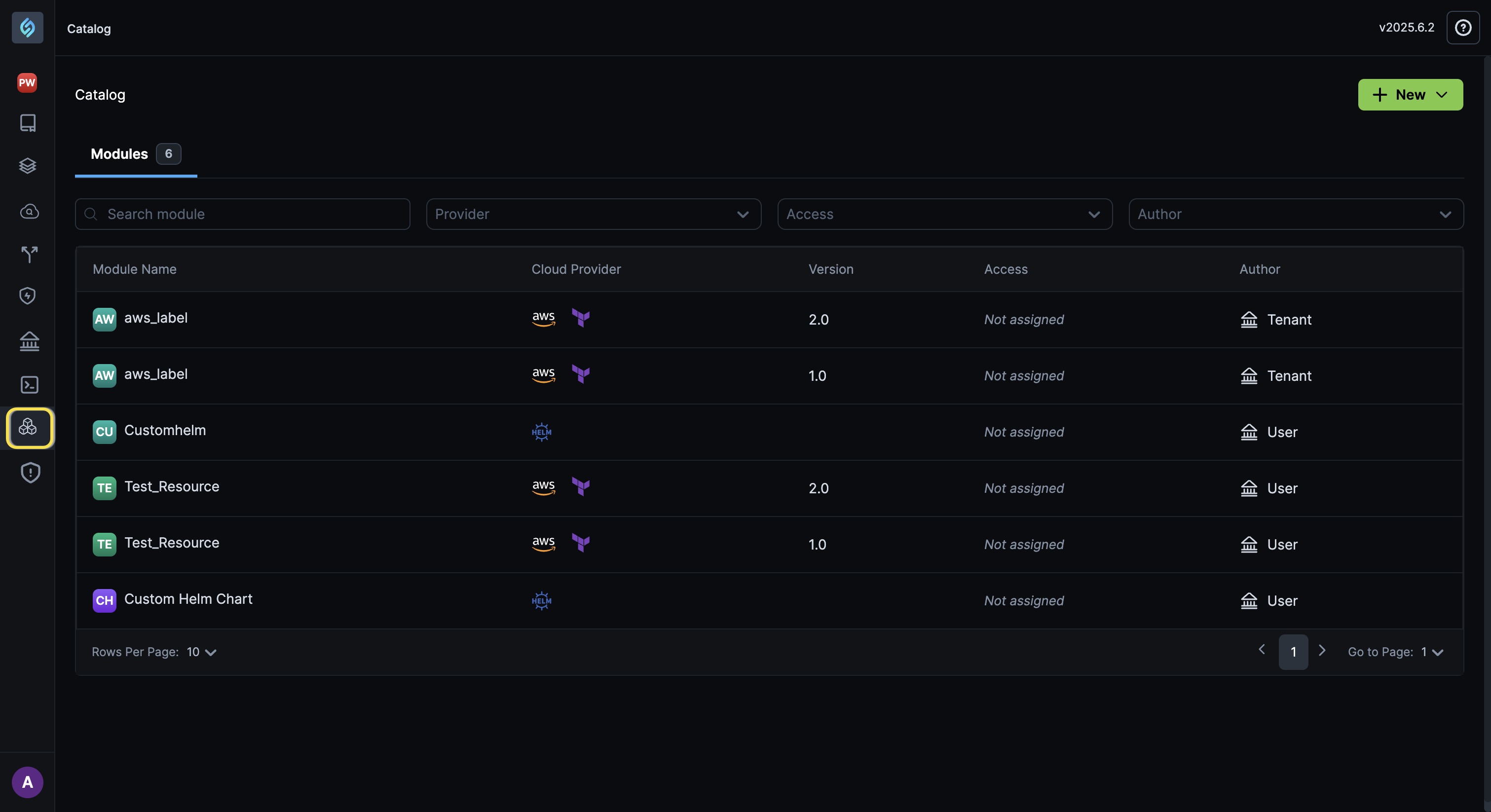
Key Features
- Centralized Module Management: The StackGen Catalog is your one-stop platform for discovering, managing, and enforcing Terraform modules from multiple sources, including custom GIT repositories, and external registries like Terraform and OpenTofu.
- Web UI and CLI: You can use either the Web UI or the CLI to ingest, list, and search Terraform modules, giving you the flexibility to interact with the catalog in the way that best suits your needs.
- RBAC Permissions: Developers can cherry-pick specific resources from an existing tfstate during appStack creation based on their RBAC permissions, ensuring only approved modules are used.
- Module Enforcement: As a DevOps team, you can enforce the usage of specific Terraform modules across different projects within your organization. This ensures consistency and control over infrastructure deployments.
Managing Access for Enterprises and Projects
- Enterprise-Level Access Management (DevOps Role) As a DevOps user, you can manage access to specific Terraform modules at the Enterprise level. This means you can set organization-wide policies to control which modules are accessible to all projects across the entire organization. This ensures that enterprise-wide configurations are secure and standardized. DevOps projects can also change access between Enterprise and Project level permissions when required.
- Project-Level Access Management (Admin Role) As an Admin user, you have the authority to assign specific Terraform modules to projects based on their needs and responsibilities. Project-level access allows you to tailor which modules are available to individual projects, ensuring they only use the relevant resources for their projects. This also includes the ability to switch access between Enterprise and Project level permissions when project requirements change.
- Switching Between Enterprise and Project Access Both DevOps and Admin users have the ability to switch between Enterprise and Project level access for Terraform modules. This flexibility allows the DevOps or Admin role users to grant or restrict access as needed based on the project scope or changes in project responsibilities. For example, DevOps users can elevate access to an enterprise-wide level for a specific module, while Admin users can narrow the access to a particular Project based on their project needs.
By managing access at both the enterprise and project levels and providing seamless transitions between these access types, StackGen Catalog ensures that your infrastructure remains secure, compliant, and streamlined across all projects within your organization.
Workflow For DevOps projects
Click to view
- Ingesting Terraform Modules
- Web UI: You can import one GIT repository at a time for custom modules through the Web UI.
- CLI: For greater flexibility, the CLI allows you to perform bulk imports for custom GIT repositories, making it easier to manage a large number of modules.
- Searching and Listing Modules Once the modules are ingested, you can list and search through the catalog. This includes modules from your custom GIT repositories, the Terraform registry, the OpenTofu registry, and StackGen autogenerated modules.
- RBAC-Enabled Module Assignment You can assign specific Terraform modules to projects based on their RBAC permissions. For example, a developer working on network controls can access StackGen autogenerated modules related to networking from the OpenTofu registry through the catalog. These modules can then be used during appStack creation.
- Enforcing Module Usage As a DevOps user, you can enforce specific Terraform modules within your organization. These enforced modules will be available to developers based on the permissions you assign to them.
tfstateImport (DevOps Responsibility) The import of tfstate files should be handled by DevOps teams. This allows DevOps teams to decide which resources should be picked into an appStack and which should not. Importing tfstate files ensures that only trusted and approved resources are included in the appStack. Developers will not have to deal with unsupported resources in this flow, as the resources imported by DevOps will be curated.
Workflow For Developer Projects
Click to view
- Accessing Modules If you’re a developer with the necessary RBAC permissions, you can access the StackGen Catalog to find the modules you need, including modules related to infrastructure resources such as networking or storage.
- Cherrypicking Resources After creating an appStack, you can overlay additional approved Terraform modules from sources like the OpenTofu registry. The modules you can access will be based on what your DevOps team has allowed through the catalog.
- Module Assignment You can assign specific modules to your projects based on project-level permissions set by the DevOps team, ensuring that only the approved resources are being used.
Known Limitations
- Web UI Import: The Web UI currently supports importing only one repository at a time for custom GIT sources. To perform bulk imports, use the CLI.
- Helm Chart Discovery: The StackGen Catalog doesn’t support Helm chart discovery through the Web UI during the initial release. You can interact with Helm charts only through the CLI for now.
- Cloud-to-Code Integration: StackGen autogenerated modules from Cloud-to-Code migrations are not included in the catalog by default. However, developers can cherry-pick specific resources from tfstate during appStack creation.
Additional Considerations
- Unsupported Resources: If a
tfstatefile includes resources that are not part of the enforced modules, these resources will be flagged as unsupported by DevOps and will not be included in the appStack. This ensures that the developer will not encounter issues with unsupported resources, as DevOps will have already curated the modules and approved them for use. - Module Removal After Assignment: If a module that was previously enforced is removed from the catalog by your DevOps team, it will be flagged with an error in the IaC tab. While the module will no longer be usable, you will still be able to export the configuration without the removed module.
- Sharing Custom vs Built-In Modules: As a DevOps team, you can differentiate between sharing custom modules and built-in modules. Custom modules can be shared selectively with projects, whereas built-in modules are automatically enforced across the organization.
Getting Started
For DevOps Projects
- Access the StackGen Catalog to import Terraform modules from custom GIT repositories, the Terraform registry, and the OpenTofu registry.
- Use the Web UI for single repository imports or the CLI for bulk imports.
- Assign and enforce specific modules for projects using RBAC permissions.
- Handle tfstate imports and ensure only approved resources are available to developers.
For Admins
- Assign access to specific projects and manage permissions for Terraform modules.
- Switch access between enterprise-wide and project-level as per organizational needs.
- Ensure the right modules are available to projects based on their roles and responsibilities.
For Developers
- Access the StackGen Catalog to search for and overlay approved Terraform modules.
- Use the catalog to discover network or storage modules, ensuring that they align with organizational policies.
- Ensure that only allowed modules are used during appStack creation.