Custom Policies
Custom Policies in StackGen allow you to define your own compliance rules tailored to your specific infrastructure requirements. These policies can be created and managed via the StackGen CLI (JSON) or through the StackGen UI (JSON or Rego (v1)), making governance accessible to both technical and non-technical team members.
With Custom Policies, you can enforce governance standards that go beyond StackGen's built-in policies. These custom policies help ensure that your cloud infrastructure meets the unique requirements of your organization.
Governance Pre-configurations
With StackGen, you can group and assign policies to projects, ensuring consistent resource management. Policies are automatically applied to appStacks created by project members.
Sample Use Case: Assign a governance pack to a project that includes:
- Read-only roles for data storage.
- Full-access roles for application hosting.
Apply Custom Policies Across Different Environments
- Use Custom Policies Across Cloud Providers: StackGen supports all cloud providers, including AWS, Azure, GCP, and Civo Cloud.
- Implement Policies on Multiple Resources: All resources supported by StackGen can be included in custom policies.
Benefits of Using Custom Policies
- Increased Flexibility: Tailor compliance and governance rules to your specific needs.
- Ensure Consistency: Apply the same governance standards across projects or the entire organization.
- Enhance Security: Enforce encryption and monitoring for sensitive resources automatically.
Custom Policy Types
There are 5 types of Custom Policies in StackGen, as described below:
| Policy Type | Description and Examples |
|---|---|
| Custom IAM Roles | Define tailored IAM roles for your resources, such as setting up read-only and audit roles for data storage resources. |
| Resources Mapping | Assign resources in your appStack based on predefined mappings, like automatically linking database references to a preferred service. |
| Resource Restriction | Control which resources different projects can use, such as limiting one project to storage and compute resources while allowing another project to access analytics tools. |
| Security and Compliance Settings | Enforce encryption and monitoring for sensitive resources and ensure compliance with organization-wide security policies. |
| Role Based Control | Configure policies for specific projects or all users, like allowing developers to access non-production resources while operations projects manage production systems. |
Create Custom Policies
StackGen provides multiple ways to create custom policies, making governance accessible to teams with different technical expertise levels. You can create policies via the CLI for maximum flexibility, or through the UI for Resource Restriction Policies and AI-assisted Resource Security Policies.
Create Policies via CLI
Click to view
Custom policies can be created using the StackGen CLI and are defined in JSON or Rego format. This method provides maximum flexibility for complex governance rules and supports all policy types.
- Custom policies are
JSONorRegobased, allowing high flexibility. - They enable both simple configurations and complex governance rules.
To learn how to create and manage custom policies via CLI, refer to the CLI Guide.
Create Policies via UI
You can create policies through the StackGen UI in two ways:
Resource Restriction Policies (UI-Based)
Click to view
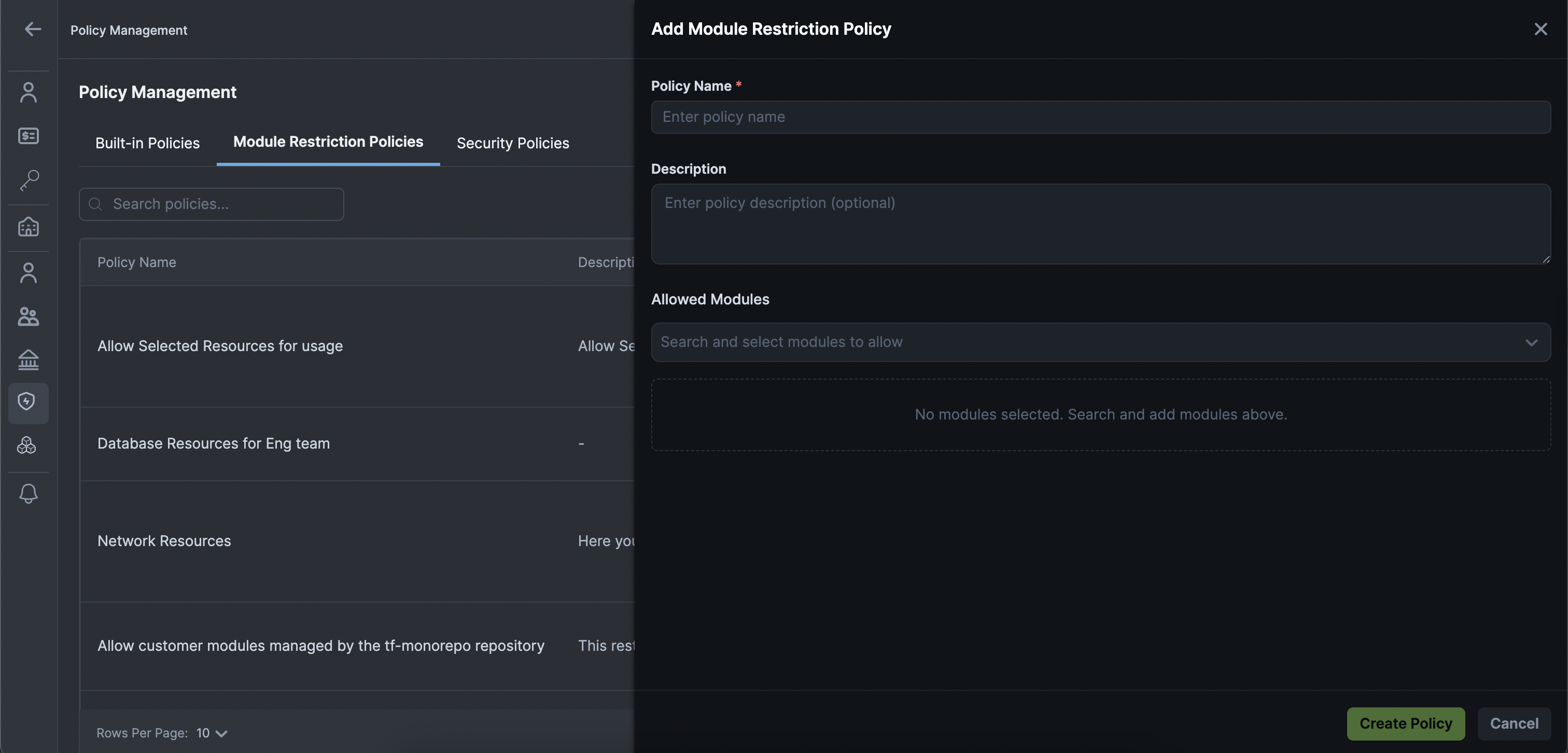
Admins can create Resource Restriction Policies directly via the StackGen UI, eliminating the need to write code for basic governance rules. This makes it easy to define which cloud resources are permitted in your organization.
Key Features:
- No Code Required: Create and manage resource restrictions through an intuitive UI, making governance accessible to non-technical team members.
- Restrict Cloud Resources: Define which cloud resources are permitted in your organization, ensuring your teams only use approved infrastructure components.
- Support Multiple Resource Types: Works with standalone, grouped, and custom resources, giving you the flexibility to control any resource type in your environment.
- Enforce at Scale: Apply organizational guardrails consistently across all projects and appStacks, making it ideal for Landing Zone and platform governance teams.
To create a Resource Restriction Policy via UI:
- Click + Add New Policy.
- Enter the Policy Name and Description.
- From the Allowed Modules dropdown, select the resources that you want to allow.
- Click Create Policy to save.
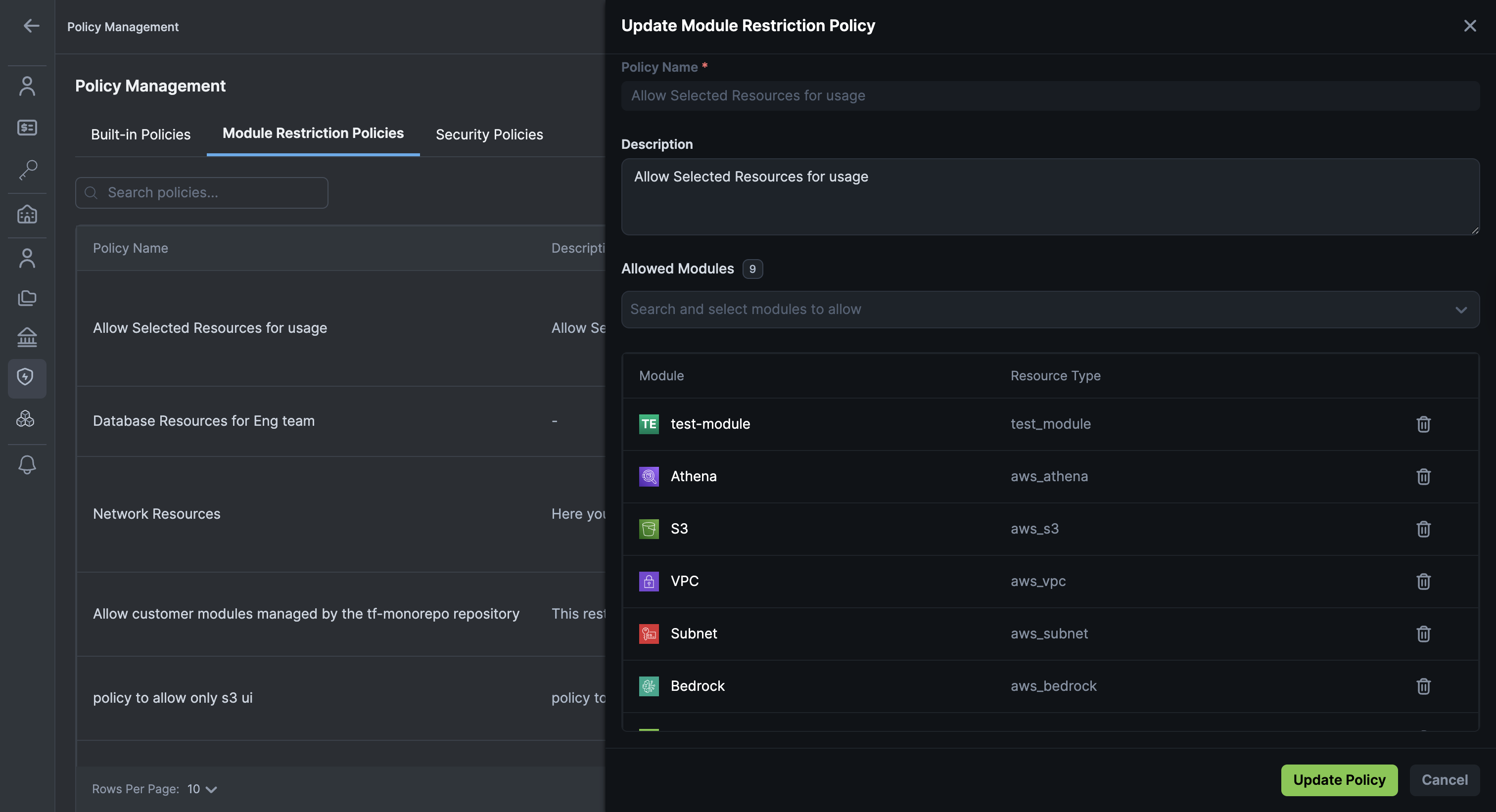
To update a Resource Restriction Policy via UI:
-
Edit the policy you want to update.
-
Add or remove allowed resource types from the Allowed Modules dropdown.
-
Click Save to apply your changes.
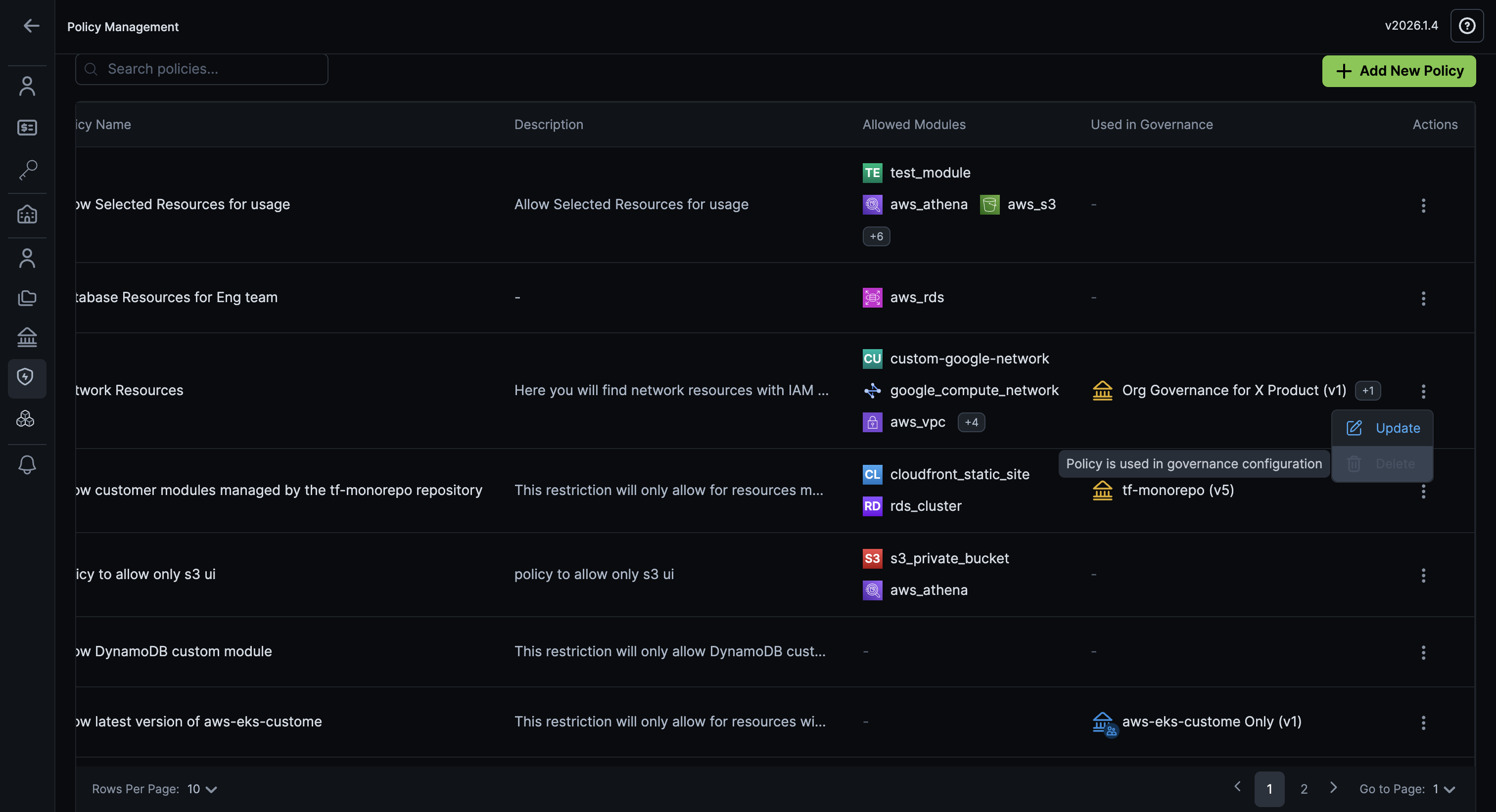
To delete a Resource Restriction Policy:
-
Click the ellipsis ⋮ icon for the Module Restriction Policy you want to delete.
-
Click Delete.
noteModule restriction policies that are currently in use cannot be deleted. You'll receive a clear warning if you attempt to delete a policy that's attached to a project or governance rule.
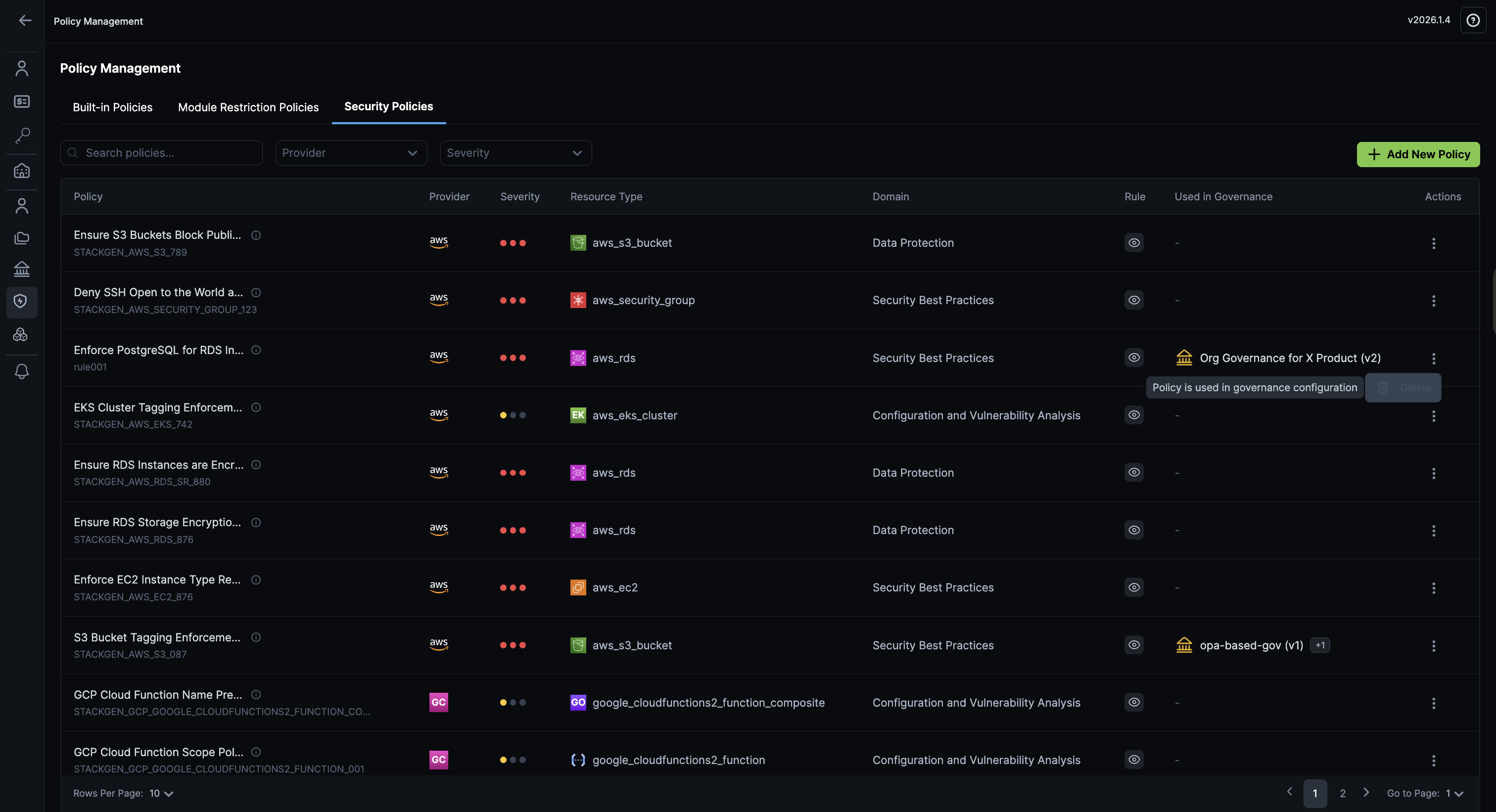
Resource Security Policies (AI-Assisted)
Click to view
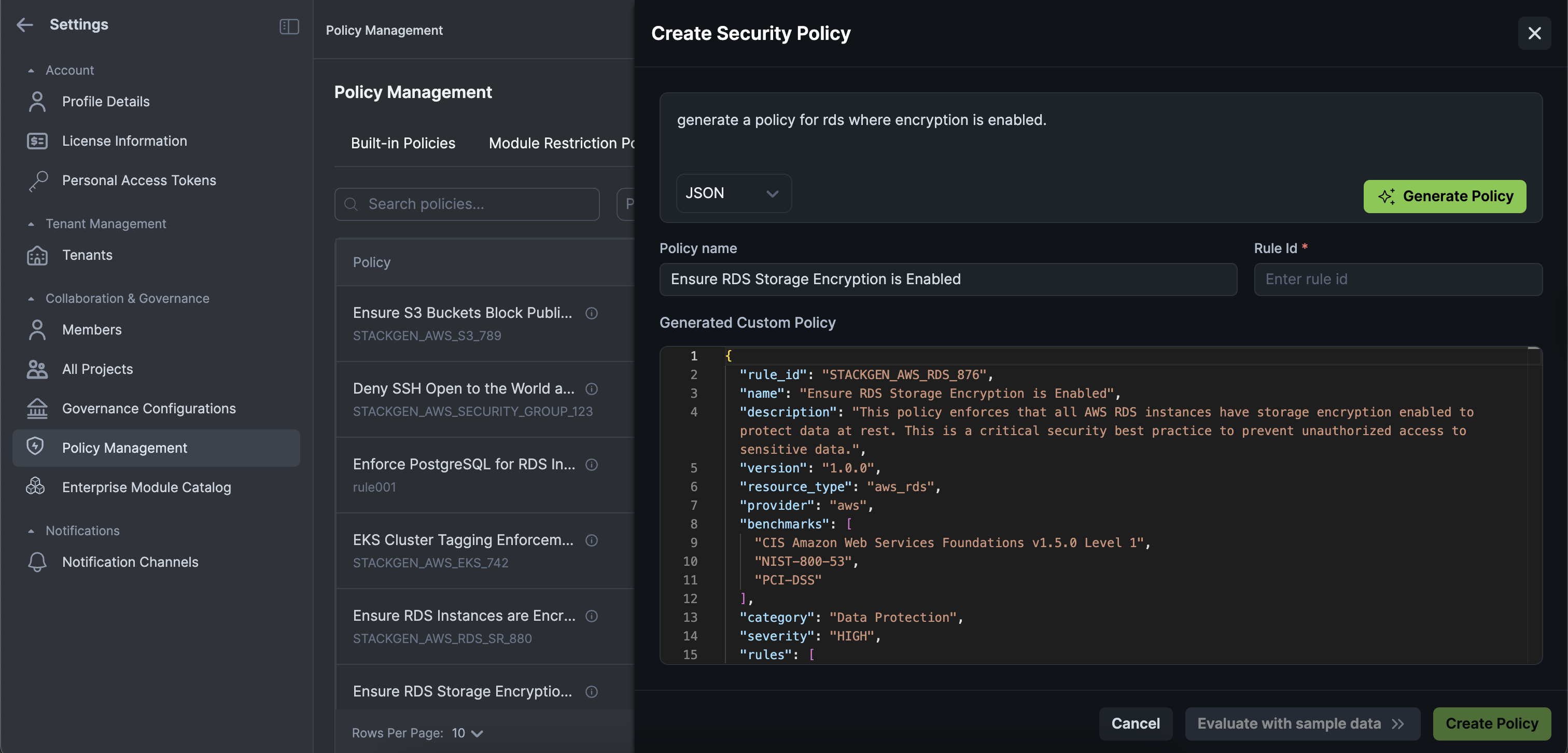
Create rules that enforce security best practices on resources using AI assistance, making policy creation faster and more accessible. The AI Assistant supports both natural language input and Rego policy conversion.
Key Features:
- Natural Language to JSON: Define policies using natural language, and StackGen automatically generates the JSON policy for you. Simply describe what you want to enforce, and the AI handles the technical translation.
- Paste Rego Support: If you prefer working with Rego policies, paste your existing Rego code and StackGen automatically generates a StackGen-compatible policy.
- Inline Validation: Test your policies with sample configurations before activation, ensuring they work as expected.
- Real-Time Feedback: Get immediate policy pass or fail feedback as you build your policies, helping you refine rules before they go live.
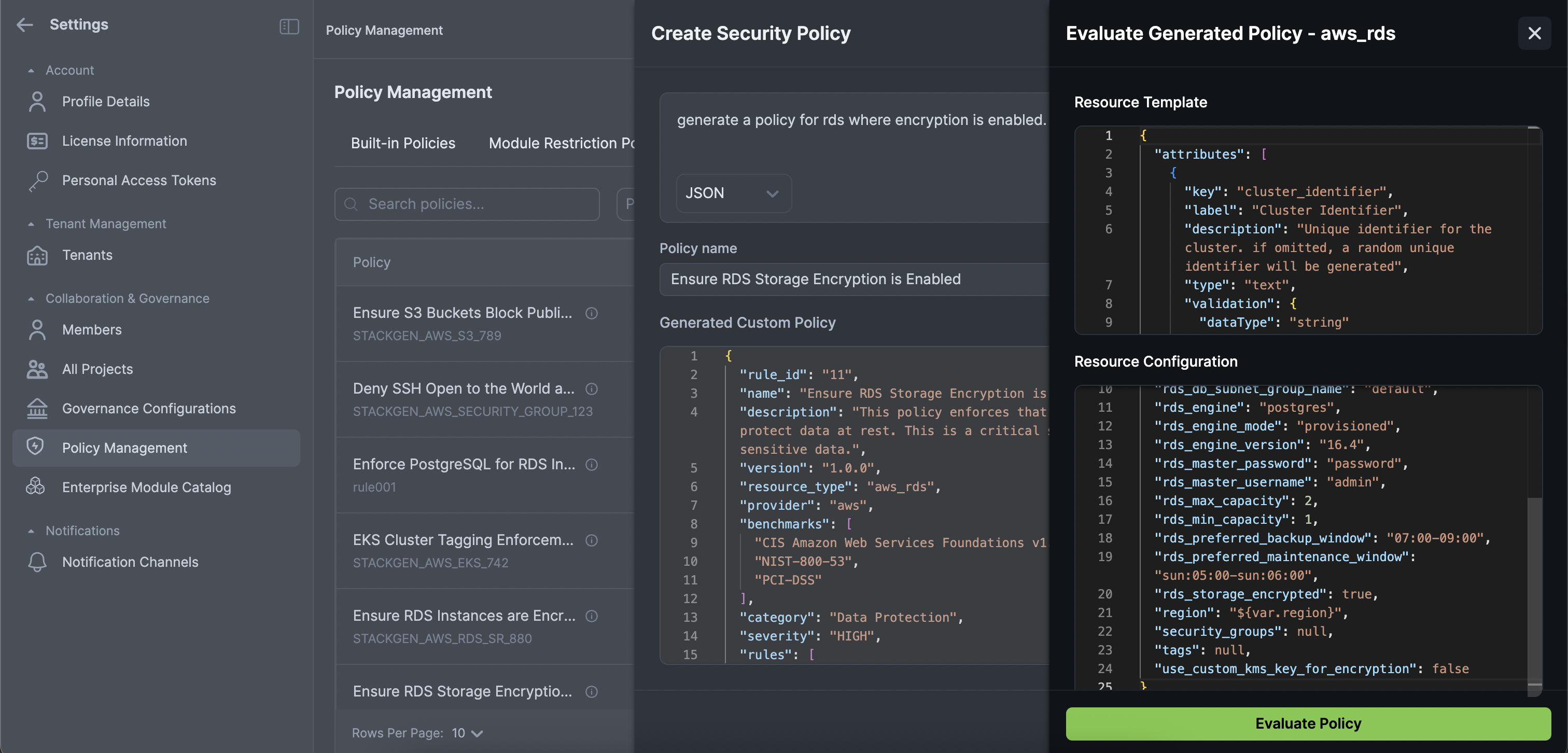
To create a Resource Security Policy using AI Assistant:
-
Enter a description of what you want to enforce in plain English (e.g., "Ensure all S3 buckets have encryption enabled") in the Generate Policy text input box. StackGen will automatically convert your input into a policy when you click Generate.
- You can choose between
jsonorRego (v1)from the output dropdown.
- You can choose between
-
Enter the Rule ID for your Policy.
-
Click Evaluate with sample data >> to test your policy:
- The Resource Template is read-only and shows the policy structure.
- Edit the Resource Configuration to test different scenarios and see how the policy behaves.
- Click Evaluate Policy to see if the policy passes or fails with real-time feedback.
-
Review the evaluation results and refine your policy if needed.
-
Once satisfied with the policy, click Create Policy to save your policy.
To delete a Resource Security Policy:
-
Click the ellipsis ⋮ icon next to the Security Policy you want to delete.
-
Click Delete.
noteSecurity policies that are currently in use cannot be deleted. You'll receive a clear warning if you attempt to delete a policy that's attached to a project or governance rule.
Apply Custom Policies to appStacks
Once created, custom policies can be applied to specific appStacks or organization-wide through the Governance Configurations page. When policies are assigned to projects, they are automatically applied to appStacks created by project members, ensuring consistent governance across your infrastructure.
Policy Evaluation Scope and Limitations
Custom policies in StackGen evaluate resources based on the data available at evaluation time. By default, policies are applied at the individual resource level.
In some scenarios, accurate compliance decisions require evaluating related or dependent resources together, for example, a security group in combination with the subnet or VPC it is associated with. When such relationships are not evaluated, policies may flag potential violations that are not actual security risks (false positives).
StackGen is evolving policy evaluation to better account for resource relationships. Until then, some policy results may require contextual review. In cases where policy results block critical workflows due to known false positives, your administrators can configure export behavior using StackGen Preference Keys.